These security cameras were hacked
Everyone wants more security, but hardly anyone wants to spend money on it. Companies like to save money on security cameras, cloud solutions and installation. Where are the risks? Insights from a software developer and integrator of security systems.
What integrators and customers should know
There are some security vulnerabilities with surveillance cameras. The government of Lithuania uncovered over 61 vulnerabilities in cameras from Dahua and Hikvision in May 2020. Among other things, data was sent to Russian servers. Manufacturers or third parties could directly access the camera streams thanks to weak passwords.
2019 Heise Online reports that students at Offenburg University of Applied Sciences have discovered a significant security vulnerability in Dahua cameras. The vulnerability CVE-2019-9677 is considered “critical”. Attackers could target the vulnerability, trigger a memory error (buffer overflow) and ultimately load and execute malicious code on cameras.
The following case, however, is not about Dahua or Hikvision, but about a leading OEM producer for video surveillance from China.
1. Fehlerhafte OEM Cloudlösung betrifft Millionen von Kameras
Hangzhou Xiongmai Technology is probably not a well known name. The Chinese company is a so-called OEM – Original Equipment Manufacturer – and produces products for the video surveillance market for over 100 companies. At the end of 2018, more than 1.3 million devices were already in use in Europe.
Serious security gap in the cloud
In 2018, Security researcher Stefan Viehböck has identified a serious security vulnerability in Xiongmai’s cloud solution for SEC Consult.
It concerns the cloud app “XMeye”.
The “XMeye P2P Cloud” function is part of the cloud app that is active by default on Xiongmai devices. This uses a protocol that allows users to access their IP camera and network recorders. This makes millions of Xiongmai surveillance cameras insecure due to the cloud feature.
- If the data transmission is not sufficiently encrypted, which unfortunately was the case en casu, any “man-in-the-middle” attacker can tap all transmitted data from the video cameras.
- The feature of the “P2P Cloud” makes it possible to bypass firewalls and easily connect to private networks.
Here you will find important information from SEC Consult that shows vulnerabilities in the default password, default user, modification of the firmware and their possible spread via the XMEye cloud.
Who is affected?
Every Xiongmai device is affected. There are more than 100 brands (are listed at the end of the article) for which Xiongmai produces.
You can identify Xiongmai devices via the web interface or on the error page (under IP/err.htm). You may see the integration of “XMEye” in apps from Goodeye, iCSee Pro, or JFeye in the product description.
It is interesting to know that the same hash algrithm is also used in Dahua products. Maybe Xiongmai was just inspired by it or the alogrithm is part of the Huawei HiSilicon Soc SDK and is used by both manufacturers?
2. US government bans products from Dahua, Hikvision and suppliers
The US is going a step further and banning products from Dahua, Hikvision and Huawei Hisilicon in federal facilities. Specifically, the US government requires its suppliers to remove Dahua, Hikvision and Huawei products (incl. OEM) from federal agency facilities.
The state-owned operator of critical infrastructure (GSA) has told its contractors to remove blacklisted equipment by 13.8.21 at the latest, otherwise existing contracts with suppliers will be terminated.
Is there a need for a blacklist in your country?
The US government’s rigorous approach also suggests a need for action in Switzerland. Are there other reasons for reconsidering cooperation ?
It also possible that the blacklist was more a political statement and part of Trump’s strategy to weaken China as a trading partner. Nevertheless, the identified security gaps are a point to seriously reconsider the cooperation with Chinese producers of security systems.
Serious security gaps also exist or existed at the Swedish company Axis or the US company Flir.
This is for sure: The topic should also be given more attention at the federal level, especially because critical infrastructures may be equipped with easily attackable products.
3. Installation, default users and default passwords
With the right evaluation and selection of products, the security risk can be minimised. easypsim is primarily a software company, but also installs video surveillance and NVR recorders itself and develops VMS and PSIM software, primarily for prisons, banks and critical infrastructures.
We are aware that our customers have the highest security requirements. That’s why we regularly check reports of security problems and exploits, and of course replace all default passwords before installation.
Our video streams are encrypted according to best practice and IT security standards. This minimises the risk of external attackers.
Measures and recommendations
Surveillance cameras can become a real security problem if basic aspects are not taken into account. With the following tips, you can reduce the risk of attacks on video cameras.
Hardware
- Was the surveillance camera manufactured by an OEM (Original Equipment Manufacturer)?
- If so, find out who manufactures the hardware components and where they were produced.
- Select a manufacturer that offers frequent and timely updates.
- The manufacturer should not have any affiliation with a national agency.
Software & Firmware
- Find out who developed the software or firmware and where it was produced.
- Ensure that updates are carried out regularly.
- Find out which channel is used to communicate security vulnerabilities.
Network settings
- Use https or rtsps streams (encrypted streams) for playback.
- Disable anonymous viewing.
- Activate IP address filtering
- Disable all ports and services that are not needed, e.g. ftp, ssh, dns, bonjour, etc.
- Segment the network and restrict access to the Internet if necessary.
Passwords
- Disable default accounts and do not use default passwords.
- Passwords should contain special characters and more than 10 characters
Scans
- Perform regular security scans of edge devices.
- Security system integrators
- Work with integrators who demonstrate a keen awareness of security vulnerabilities in surveillance cameras
- Educate yourself
- Stay on the ball and Google yourself for vulnerabilities in the products you use.
- Follow the social media profiles of manufacturers, IT security companies and experts like Stefan Viehböck @sviehb.
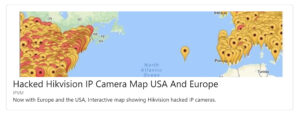
Tip: IPVM tests surveillance cameras and is a reliable source for security vulnerabilities like the Hik-Vision IP Camera Map.
In the last section of the investigation report below, it can be seen that the elimination of the sources of error has not yet enjoyed any particular priority.
Disclaimer: The article is based on the cited/linked reports. It is to be hoped that all security vulnerabilities have been fixed by today. Hope because the author has not been able to find out conclusively whether all the security gaps mentioned have been closed or whether those responsible are in the process of closing them.
OEM Marken: 9Trading, Abowone, AHWVSE, ANRAN, ASECAM, Autoeye, AZISHN, A-ZONE, BESDER/BESDERSEC, BESSKY, Bestmo, BFMore, BOAVISION, BULWARK, CANAVIS, CWH, DAGRO, datocctv, DEFEWAY, digoo, DiySecurityCameraWorld, DONPHIA, ENKLOV, ESAMACT, ESCAM, EVTEVISION, Fayele, FLOUREON , Funi, GADINAN, GARUNK, HAMROL, HAMROLTE, Highfly, Hiseeu, HISVISION, HMQC, IHOMEGUARD, ISSEUSEE, iTooner, JENNOV, Jooan, Jshida, JUESENWDM, JUFENG, JZTEK, KERUI, KKMOON, KONLEN, Kopda, Lenyes, LESHP, LEVCOECAM, LINGSEE, LOOSAFE, MIEBUL, MISECU, Nextrend, OEM, OLOEY, OUERTECH, QNTSQ, SACAM, SANNCE, SANSCO, SecTec, Shell film, Sifvision / sifsecurityvision, smar, SMTSEC, SSICON, SUNBA, Sunivision, Susikum, TECBOX, Techage, Techege, TianAnXun, TMEZON, TVPSii, Unique Vision, unitoptek, USAFEQLO, VOLDRELI, Westmile, Westshine, Wistino, Witrue, WNK Security Technology, WOFEA, WOSHIJIA, WUSONLUSAN, XIAO MA, XinAnX, xloongx, YiiSPO, YUCHENG, YUNSYE, zclever, zilnk, ZJUXIN, zmodo, ZRHUNTER
Information from this article are mainly contributed by Stefan Viehböck (@sviehb) on behalf of SEC Consult Vulnerability Lab, Heise.de, IPVM.